Android Malware and Analysis: Dunham, Ken, Hartman, Shane, Quintans, Manu, Morales, Jose Andre, Strazzere, Tim: 9781482252194: Amazon.com: Books
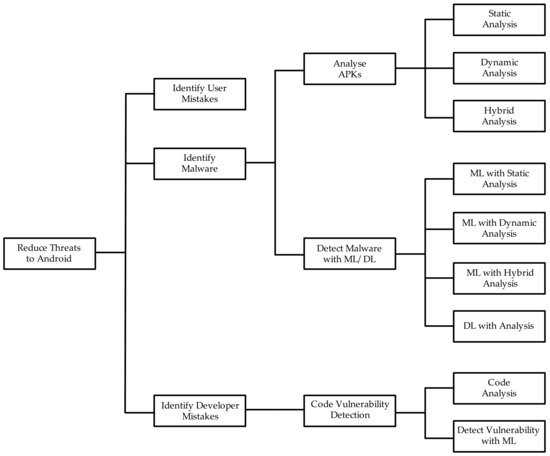
Electronics | Free Full-Text | Android Mobile Malware Detection Using Machine Learning: A Systematic Review






![PDF] Evaluating Smartphone Application Security : A Case Study on Android | Semantic Scholar PDF] Evaluating Smartphone Application Security : A Case Study on Android | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c89ca7704f9020da92ca487007e8d52ceddf07d9/5-Figure5-1.png)